
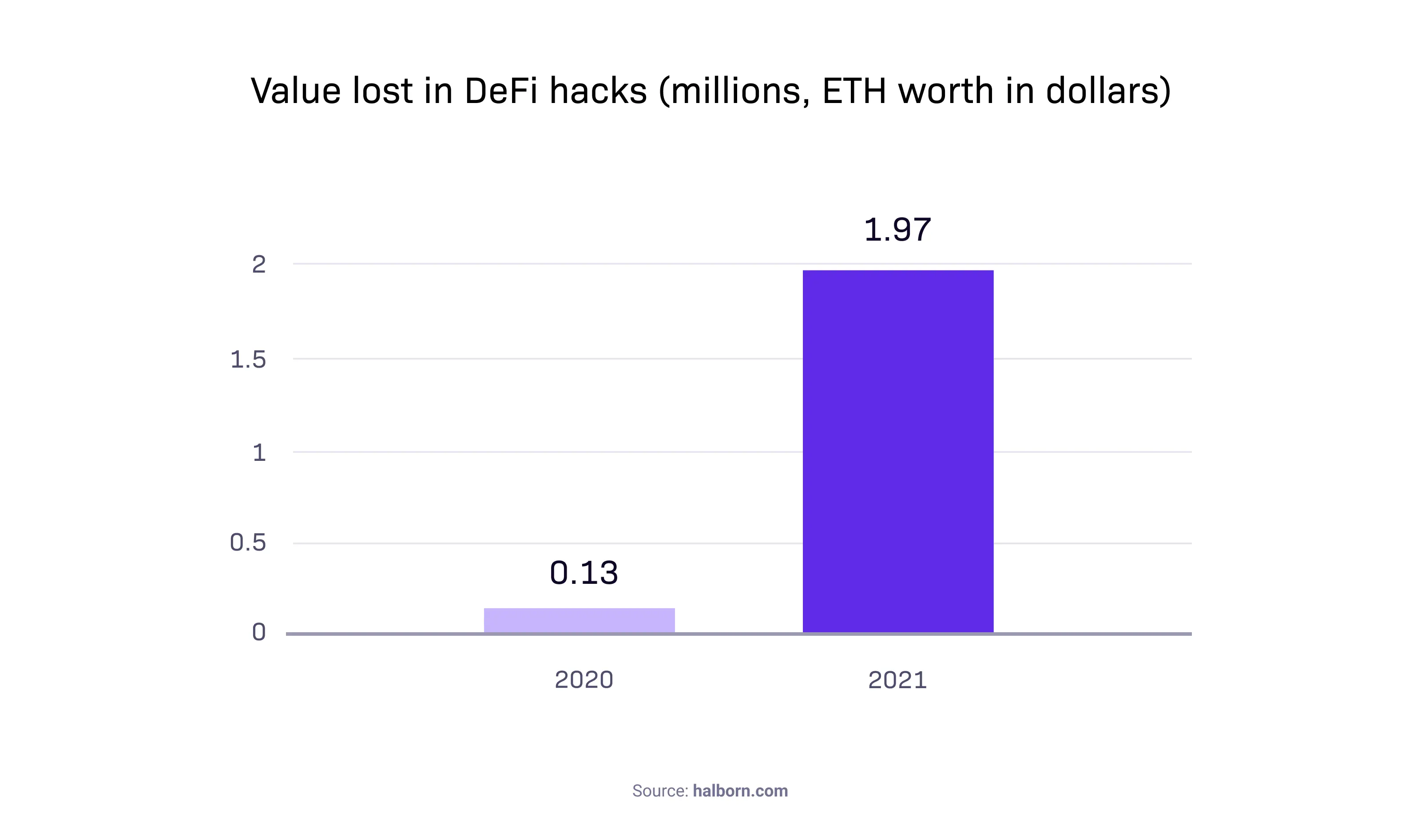
You've most likely come here because you're getting ready to deploy your Ethereum blockchain app. Regarding the rampant frenzy of smart contracts, it's a smart move (pun intended). While many have a longing for them nowadays, only very few prioritize quality over quantity and patience over bravado. The rest make expensive mistakes. Due to smart contract errors, nearly $2 billion was lost on decentralized finance platforms in 2021 alone. In this article, we'll discuss the security issues and best practices in smart contract development. After all, you don’t want to get outsmarted, do you?
Vulnerabilities in Smart Contracts
When speaking of blockchain security, let’s delve into one of the most heinous smart contracts exploits ever conducted. On November 8th, 2017, a man going by the alias Devops199 created a Github issue for Parity Technologies, a blockchain company. The title of the issue was "anyone can kill your contract."
Devops199 apparently discovered a bug in a multi-signature contract that had been used as a digital wallet by a large number of people to safely store their Ethereum. That bug, or rather a smart contract vulnerability, had the potential to make him the contract's owner. Then everything fell apart.
The careless programmer killed the contract by deleting the function that allowed Ethereum owners to transfer their assets. He appeared to have permanently locked the assets in the contract, rendering it completely useless. What was the value of Ethereum in these contracts? Estimates range from $150 million to $300 million.
Unfortunately, it was not a one-time occurrence. We hear about similar security vulnerabilities involving DeFi projects several times a month. According to Rekt.News, at least two major exploits have already occurred in May 2022. Fei Rari, a DeFi lender, lost $80 million in a hack attack, while Saddle Finance fell victim to some unscrupulous swindlers who stole $11 million.
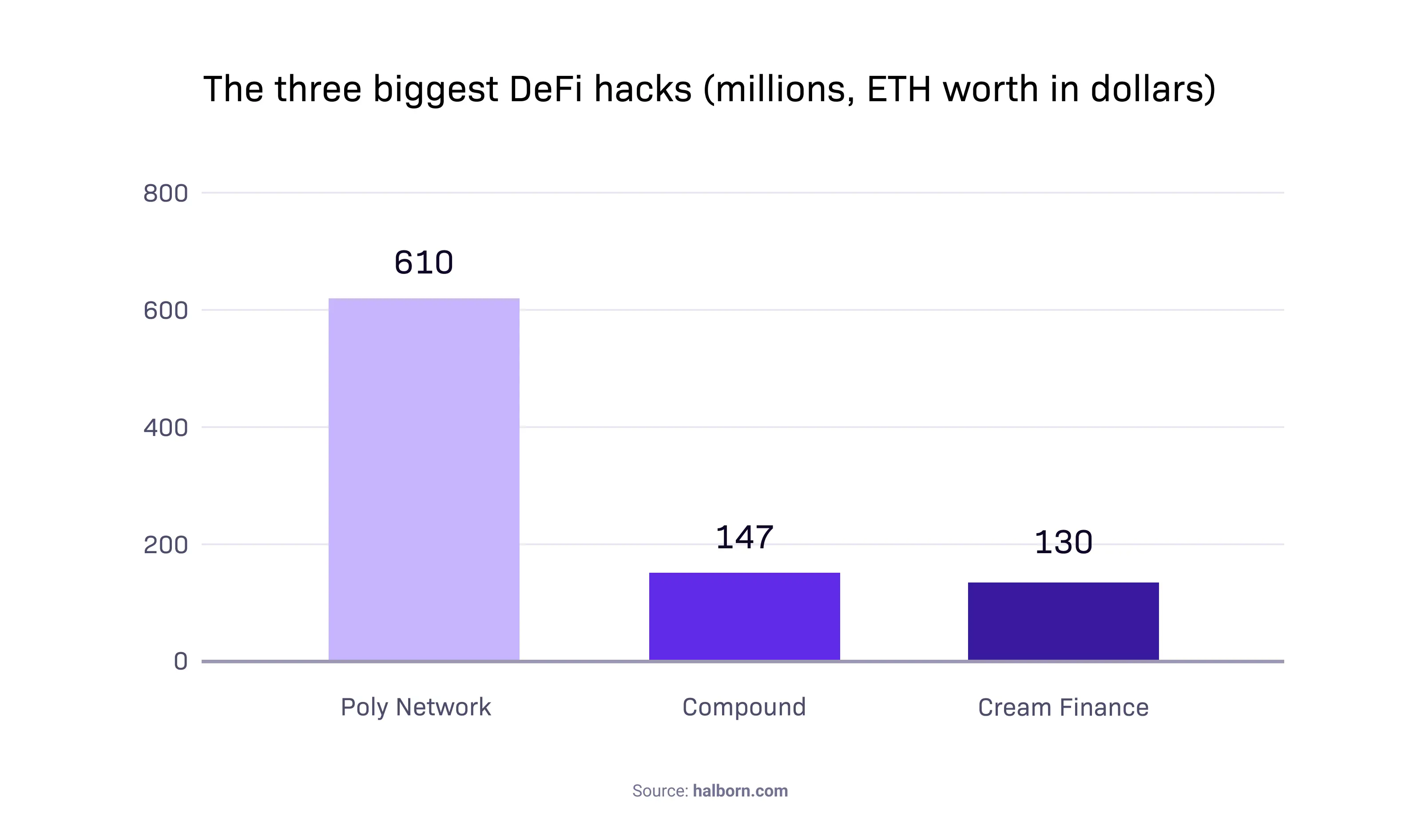
But the DeFi industry's largest and most infamous hack occurred back in August 2021. The attacker compromised a smart contract on the Poly Network platform and transferred a total of $610 million to their Ethereum and BSC addresses.
Compound Finance, the Ethereum-based lending and borrowing protocol, comes second (or second-worst) in this ranking. On September 30, 2021, the protocol paid out large sums in its native cryptocurrency COMP to some users who took advantage of a flaw in the protocol's smart contract, draining $147 million.
It's worth mentioning Cream Finance, a multi-chain lending protocol, suffered an attack in late October 2021 that wiped out $130 million from its Ethereum-based liquidity. And sadly, the list goes on.
You may be wondering, "Why does this happen?" We need to look more closely at smart contracts to get a better understanding of them.
Ethereum Smart Contracts: the Background
What exactly are Smart Contracts?
Smart contracts are agreements between two parties without the need for a trusted third party. These contracts have the unique ability to transfer ether to and from users as well as other contracts.
Ethereum is the most popular smart contract architecture, in which smart contracts are represented as computer programs. The Ethereum consensus protocol, which governs how the peer-to-peer network's nodes expand the blockchain, aims to ensure that contracts are executed correctly.
Nodes must enter a “lottery” to add a new block of data to the blockchain, with the likelihood of winning proportional to the computational capacity of the node. Even if a malevolent node wins the mining game and tries to append a block containing improper contract executions, the block will eventually be purged from the blockchain unless this person has more than 51% of network mining capacity to keep his fake block high enough.
Programming Smart Contracts
Fields and functions are the building blocks of contracts. By delivering a proper transaction to the Ethereum nodes, a user can call a function. The transaction must include the miners' execution fee, optionally a transfer of ether from the caller to the contract.
The contract can accept ether from other users and send it to them using the transfer function. The hashtable outflow records all the addresses to which it sends money, and associates to each of them the total transferred amount. The contract holds all of the ether received. Its value is instantly added to the balance sheet..
Solidity Smart Contracts
There are various reasons why smart contract development in Ethereum is particularly prone to failure. Many of them are linked to Solidity, Ethereum's high-level programming language. It is used in the Ethereum Virtual Machine (EVM), which helps implement most smart contracts.
A discrepancy between Solidity's semantics and programmers' perception shows signs of being the source of many problems. The issue is that, while Solidity appears to be a typed Javascript-like language, it implements exceptions and functions in an unusual way.
Apart from that, there is still a need for a complete, self-contained, and up-to-date study of Ethereum smart contract vulnerabilities.
Smart Contract Security
Smart Contract Security Refers to the proper execution of Ethereum smart contracts is a requirement for their effectiveness. However, the correctness of executions alone is not enough to ensure the security of smart contracts. Therefore, there are various security flaws with Ethereum.
Ethereum Smart Contract Vulnerabilities Exist
As previously stated, Solidity is to blame for some of the issues affecting smart contract security, but the list of difficulties does not end there. That this is the fault of how VM works with the state and how external calls are invoked.
Let’s take a closer look at the types of vulnerabilities in Ethereum smart contracts security.
Reentrancy Attacks
Reentrancy is regarded as one of the most devastating smart contract attack strategies. This assault method is capable of completely destroying the contract or stealing sensitive information.
When a function calls for another contract via an outer call, reentrancy can occur. An attacker can use this flaw to run a recursive callback of the main function, resulting in an unwanted loop that is repeated several times.
Application Bugs
The error issue in the smart contract code can cause application bug exploitation. This type of exploitation is most common in smart contracts. It occurs when decentralized application developers fail to identify code problems. Through simple programming flaws, attackers can deplete the contract wallet of all funds.
Malicious Users
Spreading malware to fool consumers is a form of malicious behavior. This is usually done over the Internet in order to compromise a user's identity or commit fraud by using malware or viruses. Malicious attacks could take the form of an email from the wallet requesting that the account be synced with a network that has recently hard-forked.
Another possibility is any other bogus website that asks you to connect your wallet and send money somewhere. An attacker may be able to drain all of the currency from a user's wallet by exploiting it through malicious attacks.
Flaws in the Protocol
To keep the network running, the blockchain includes a consensus protocol. Exploits based on poor consensus have been increasingly common in recent years, despite the fact that attacks based on flaws in consensus protocols can be quite costly.
Successful assaults, on the other hand, can remove blocks from the chain, completely destroy a blockchain, or gain complete control over the price of a coin. Weak protocols lead to attack strategies such as 51 percent attack, selfish mining, and 34 percent assault.
The Timestamp
Another issue that dishonest miners can exploit is timestamp dependency. A miner may rearrange the timestamp by a few seconds in order to obtain an advantage. The timestamp dependency issue is caused by a faulty understanding of timekeeping. It allows the Ethereum network to be decoupled from the globally synchronized clock.

Security Tools: How to Improve Smart Contract Security
Smart contract security, like any other program, is based on the same principles of coding, testing, and ensuring. Below are our tips for what you should do to improve your smart contract security.
Smart Contract Audit and Testing
During the creation of your blockchain software, you won't be able to see everything. That is why it is critical to run preliminary tests. It's in your best interest to use all of the testing tools accessible to you. You should begin with simple contract functionality testing, and even launch a smart contract on a test network. All of these processes can greatly improve your odds of discovering serious flaws in your code while they're still fixable.
Security audits are yet another necessary step in ensuring your smart contract security. This is because expert auditors are likely to not only uncover potential flaws in your code but also provide you with helpful suggestions on how to improve and optimize it.
Smart Contract Developers
Though the internet is filled with many beneficial tools for highlighting potential faults in your code, it cannot be considered a replacement for a competent and experienced blockchain development team.
Hackers can always find a method to exploit potential gaps in your smart contract security, even if your smart contract seems bug-free and secure. They can corrupt a smart contract code or even an entire blockchain platform, draining thousands or even millions of dollars in cryptocurrencies.
Collaboration with an experienced team that has many projects under its belt, will help you go through the development process, identify potential challenges and launch the whole pallet of decentralized applications that will mark your name.
Now You Know Smart Contract Security Best Practices
Smart contracts are at the very edge of blockchain technology, with applications in almost every industry. Because smart contracts deal with and transfer high-value assets, it's vital that their implementation is secure against attacks aimed at stealing or interfering with the assets.
As the name implies, a smart contract is smart yet fragile. Its vulnerability manifests itself in a variety of ways, ranging from coding errors and protocol flaws to being vulnerable to malicious attacks and reentrancy attacks.
There is no single reliable method for ensuring the security of smart contracts, just as there is no single reliable method for ensuring the security of any technological novelties.
Simply said, a smart contract is safe when it has been created by a reputable blockchain development team. Security audits and testing are another technique to keep smart contracts safe.
Deploying smart contracts too quickly and without the necessary security checks can get you into serious trouble. After all, the staggering figure of $2 billion worth of missing ETH was far from an accident.




