
With the growing popularization of containerization and cloud architecture, we face a vast amount of security issues, which are still not commonly understood by most engineers. Furthermore, by using public images, we put great trust in their creators. Most of the time we lack the manpower to actually check these Docker images properly and even if we do it once, we need to be aware that they will soon become outdated. Seeing the necessity to react to each new common vulnerability and exposure (CVE), and the tight race between security teams and cybercriminals wishing to use the system vulnerabilities to their advantage, we can draw the conclusion that automatization is the key to success. Fortunately, there are many tools that can make it simple and painless.
Comparison of the most popular security tools
In the enormous market of security, we decided to pick up a few tools that are either the most popular or caught our attention due to specific unique features. In the comparison below the tools have been sorted and grouped by their complexity and price.
Open-source, free to use tools that are a good solution for CI/CD:
- Trivy
- Anchore
- Clair
Those built on top of the open-source tools provide an additional level of abstraction and make integration easier:
- Docker Hub Vulnerability Scanning
- AWS ECR
The below tools are more complex and will scan your images, but also go much further in their security offer:
- Sysdig
- Snyk
Open-source tools
Trivy
Trivy makes a good impression. It’s easy to use, it’s fast and it’s free. Trivy will let you scan images, file systems and repositories for any vulnerabilities and issues. It will detect CVEs of OS packages, applications susceptibilities, and exposures of IaC in Terraform files, Kubernetes and Docker. It will take you less than a minute to install on a local machine and an equal amount of time to include in CI/CD. It’s also available as self-service. It can be deployed from helm, docker or ECR.
To install Trivy use the commands below:
sudo apt-get install wget apt-transport-https gnupg lsb-release
wget -qO - https://aquasecurity.github.io/trivy-repo/deb/public.key | sudo apt-key add -
echo deb https://aquasecurity.github.io/trivy-repo/deb $(lsb_release -sc) main | sudo tee -a /etc/apt/sources.list.d/trivy.list
sudo apt-get update
sudo apt-get install trivyRun the command to scan an image:
trivy image alpine:3.10.7
You can also run Trivy to scan your code:
trivy config ./directory-with-dockerfiles/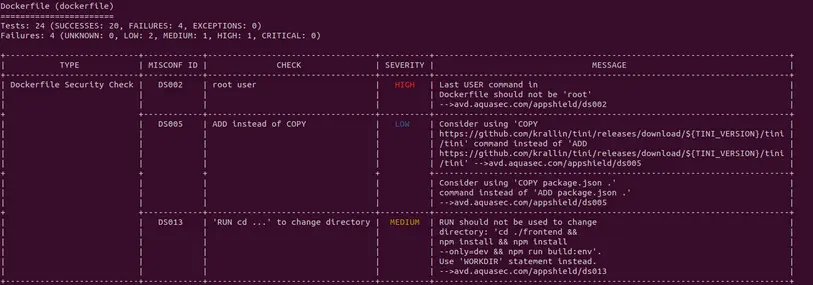
trivy conf --severity HIGH ./direcorty-with-k8s-yamls/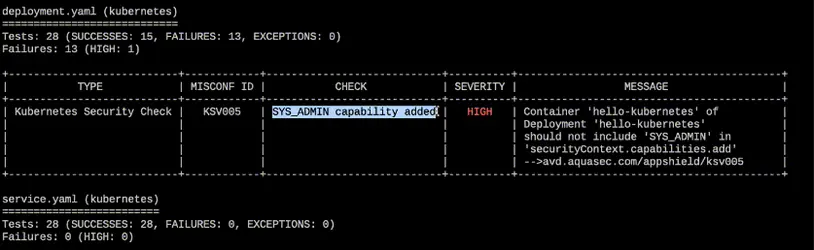
Anchore
The Anchore Engine is an open-source project that provides a centralized service for inspection, analysis, and certification of container images. It can be used as a standalone, CI/CD service or REST API. A service that analyzes docker images and applies user-defined acceptance policies to allow automated container image validation and certification.
This tool can provide you with a completely different experience on the free tier than on the paid tier. Obviously, let’s start from the free tier. Here, you receive a scanning tool similar to what you would get with Trivy. However, it’s significantly slower, the process of using it is more cumbersome, the output is less friendly and most importantly, it scans fewer CVEs.
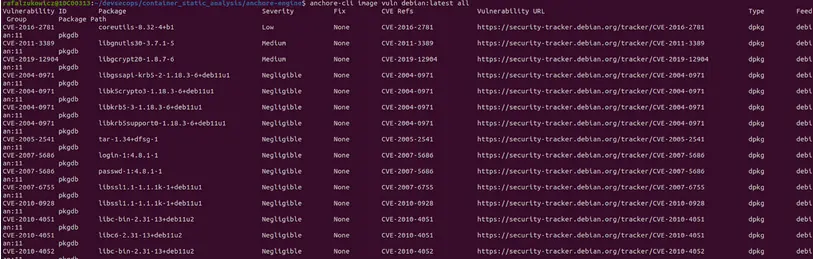
Scanning with CLI on a local machine
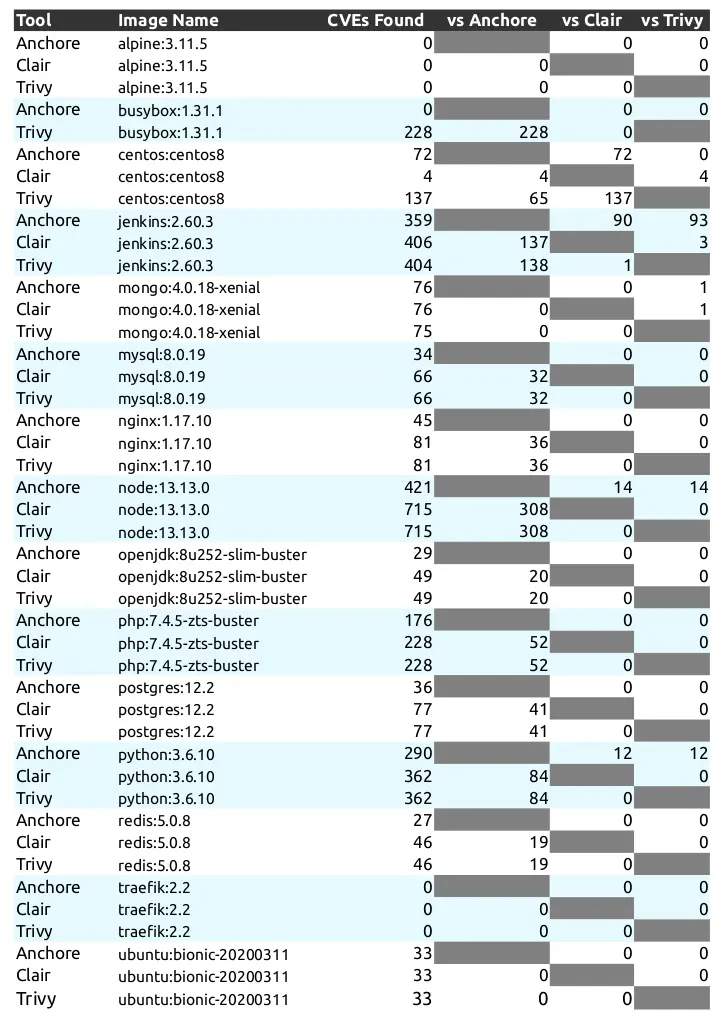
Comparison of CVEs detected Anchore vs Clair vs Trivy
Source: a10o.net
Anchore can also be used in a paid version. Here, we receive a graphical platform with additional features like data vulnerability scanning, compliance & audit, integration with Slack, Jira, GitHub and the ability to generate a comprehensive Software Bill of Materials (SBOM). However, they use a hidden price policy and, with a considerably lower score than Clair or Trivy, it’s a doubtful choice.

Anchor image scanning with the graphical user interface
Clair
Clair is an open-source container static vulnerability analyzer and the most popular open-source scanning tool. As seen in the comparison above it tops Anchor and has similar results to Trivy. However, it takes a lot of time to run as CLI. Starting Clair from scratch takes about 20 to 30 minutes because the database needs to be filled up with CVEs. Clair needs to access the container layers and therefore you need remote access from Clair to your build job. It’s much more suited to work as a standalone service. I would personally recommend Trivy as it’s easier to use and gives similar results. Nevertheless, that’s a matter of personal preference and choosing Clair should also be considered as a valid option.

Clair scanning example
Implementation and maintenance tools
We are switching from open-source tools to services that implement them and relieve us from the additional burden of maintaining and implementing many solutions.
AWS ECR
AWS ECR in the background uses Clair in the background. This solves the problems of the tool’s complexity and negates the time-consuming process of updating the database for Clair. We have an option to scan images on the push for $0.09 per scan or scan them actively each time when a new CVEs is released for an additional $0.01 per active scan. The Enhanced scanning allows checking for programing language package vulnerabilities as well. For any project that is already relying on AWS infrastructure, AWS ECR seems like a natural choice. It allows for easy integration with other AWS resources, for example by sending notifications through EventBridge to Slack. For the how-to part, I’ll do my best to send you directly to AWS docs where the whole process is well described. Regarding the effectiveness of the tool since it’s based on Clair we can expect a high amount of detected CVEs.

ECR scanning example
Docker Hub Vulnerability Scanner
Docker Hub Vulnerability Scanner seems like a natural choice for many companies utilizing Docker Hub. The scanner itself is an implementation of another open-source tool Snyk which provides good coverage of known security issues of container images. For many teams who are just beginning to use the scanning capabilities it’s just a matter of activating that feature on their account. Nevertheless, it’s only accessible on the paid tier of Docker, so the decision might be dependent on the financial aspect. With the new Docker policy for many, it might be obligatory to switch to paid version either way. For smaller teams and cost-aware projects, I would recommend choosing either Trivy or Clair.

Docker Hub scanning example

Docker Hub scanning example
Snyk
Snyk offers a security solution specifically designed with developers in mind. It searches for license violations in Docker images and provides a vulnerability report for each package in a repository. It’s simple to use, easy to implement and it’s built on top open-source tools such as TravisCI, Falco, etc. It’s trusted by a lot of big players like Google, Datadog, Revolut, Salesforce and ATLASSIAN to name just a few. In addition to scanning for vulnerabilities of images, it also provides scanners for networks, web applications, IaC, Kubernetes files and open-source dependencies. To start using it simply create an account in Snyk and connect it with your repository. Snyk will start building the application and scan for weaknesses automatically. The feature that you’re likely to love is the auto pull request which fixes dangerous or outdated dependencies. The paid tier also allows for monitoring, integration with many tools, policy compliance, SSO, self-service. The free-tier is unfortunately limited in the number of executions which might not be sufficient after some time, and the current prices for paid tiers are notably higher than what you would pay using competitive tools.
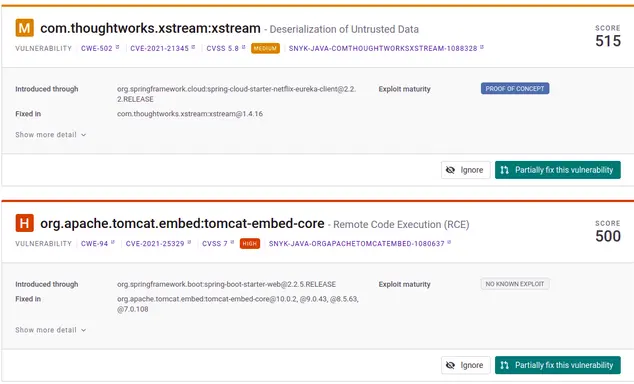
Fix vulnerability autocommit

Example of a connected and scanned repository in Snyk
SysDig
SySDig offers scanning and monitoring solutions dedicated to Enterprise teams and provides container security across the whole lifecycle. It automatically discovers cloud assets including systems, applications, and services. It also enables users to flag misconfigurations of IaC, CI/CD, registries, applications, cloud resources, Kubernetes and detect unexpected changes and suspicious behaviour by parsing Cloud logs. It’s a far more complex tool than those mentioned above.
SysDig allows for scanning for vulnerabilities of IaC, CI/CD, registries, applications, cloud resources, and Kubernetes. Furthermore, it creates an elaborated Cloud Security system. It will allow for constant monitoring of all cloud architecture including Kubernetes and the recreation of hostile actions on short-lived containers. It also allows for validation against compliance NIST, PCI, SOC2, or HIPAA NIST 800-53, PCI DSS, SOC 2, MITRE ATT&CK®, CIS AWS, and AWS Foundational Security Best Practices. Allows for integration with your SIEM and SOAR platforms. It automatically builds and customizes policies, implements least-privilege and compliant network policies, stimulates and visualizes network communication. The disadvantage of the solution is that it relies on additional AWS resources which have to be deployed on the client infrastructure which might be in contradiction to many companies’ policies. In order to include SysDig as part of your system you also need to use Terraform which is not implemented by all companies. If you want to try SysDig you have to create an account and copy the module definition to your Terraform main file:
module "secure-for-cloud_example_single-account" {
source = "sysdiglabs/secure-for-cloud/aws//examples/single-account"
sysdig_secure_endpoint = "https://us2.app.sysdig.com"
sysdig_secure_api_token = "your-token-from-sysdig"
}
And then run:
terraform apply
There are some additional steps that you have to accomplish in your SysDig account in order to fully use its capabilities and you have to expect that it will take a few hours. Nevertheless, the steps are well described and when I was stuck in one of them the support turned out to be very responsive and helped me solve the issue. Considering all the features that SysDig can give you, the price is very attractive and can be recommended as the next step for companies that care about security.
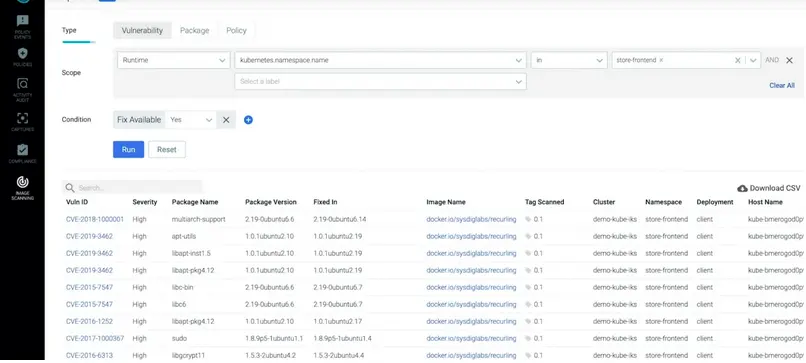
SysDig image scanning
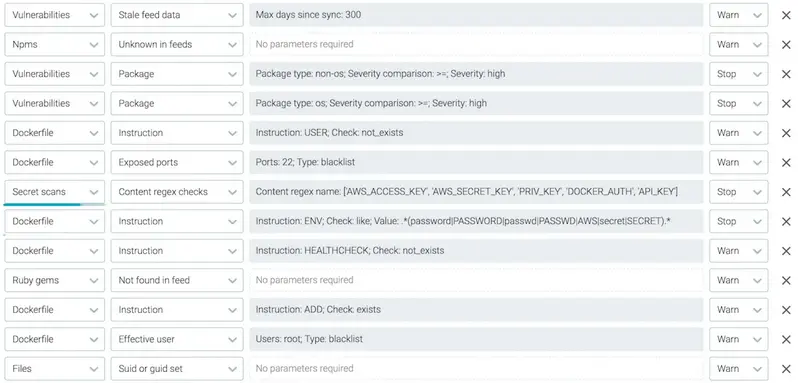
SysDig policy compliances

SysDig K8s monitoring
So which one should you go for?
Below is a handy summary that will hopefully help you to decide.

In the end, it’s not easy to give an unequivocal verdict. Nevertheless, I would recommend implementing Trivy as part of CI/CD, using SysDig for advanced cloud protection and AWS ECR for scanning projects heavily relying on AWS or Docker Hub Vulnerability scanning if your team already has to pay for a Docker account.



